- Topic1/3
14k Popularity
34k Popularity
17k Popularity
6k Popularity
172k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is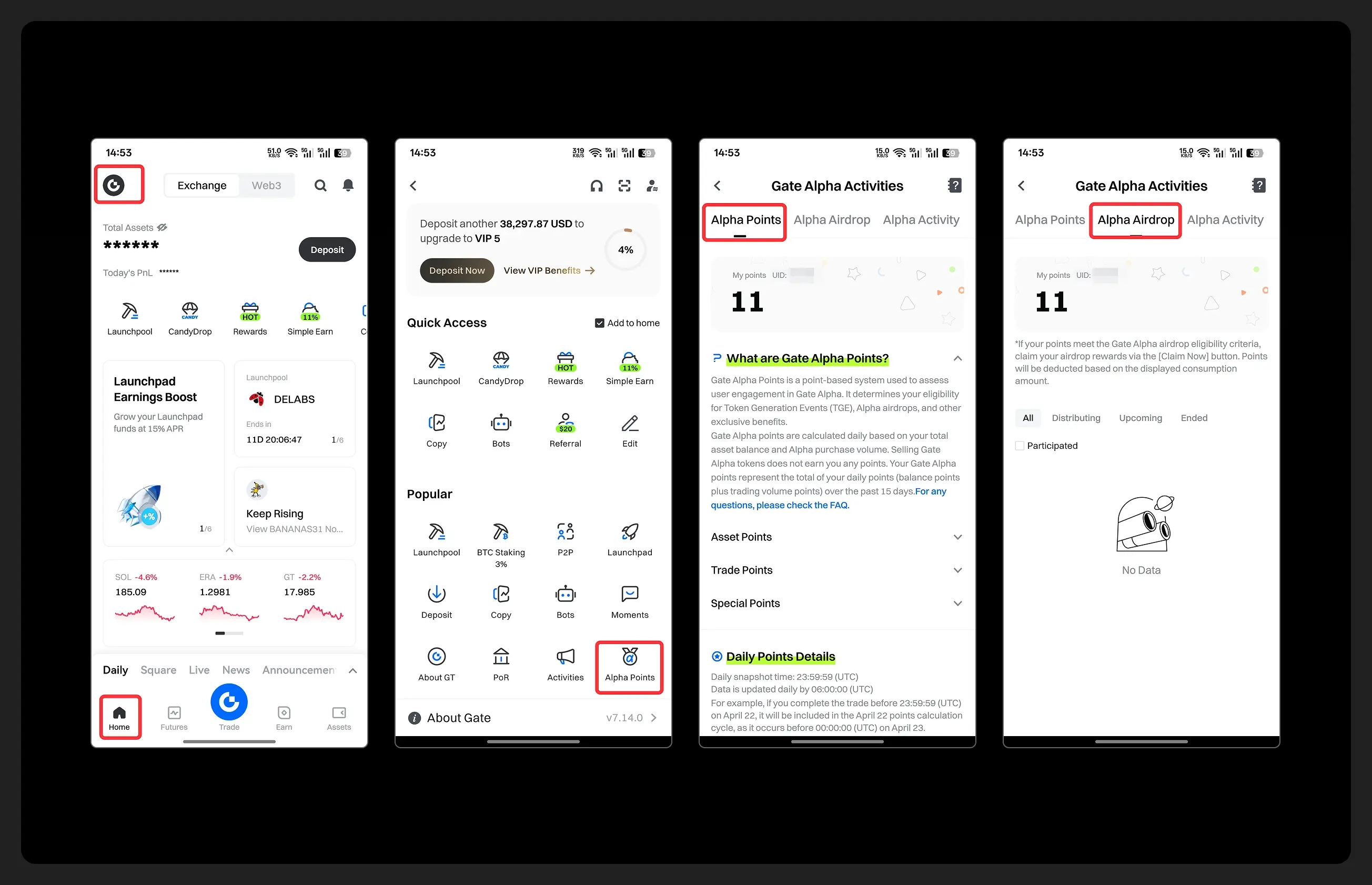
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Drainer Software Rampant: Analysis of Newbie Methods in Crypto Assets Fraud
New Trends in Crypto Assets Scams: The Proliferation of Drainer Software
Recently, phishing attacks in the Crypto Assets field have shown explosive growth, one important reason being the widespread use of Drainer software. Drainer is a malicious program specifically designed to illegally empty cryptocurrency wallets, and its developers provide it to criminals through a rental service, allowing anyone who pays to access this dangerous tool.
This article will introduce several typical Drainer operation modes, and through analyzing real cases, help users enhance their awareness of phishing threats.
Main Methods of Operation of Drainer
Although there are many types of Drainers, their basic patterns are quite similar - mainly using social engineering techniques, such as forging official announcements or airdrop activities, to lure users into falling for scams.
Fake Airdrop Claim
A certain Drainer gang promotes its services through Telegram channels, adopting an "scam-as-a-service" operational model. Developers provide phishing websites for scammers to support their illegal activities. Once victims scan the QR code on the phishing site and connect their wallets, the Drainer automatically detects and locks the most valuable and easily transferable assets in the wallet, initiating malicious transactions. When victims confirm these transactions, the assets are transferred to the criminals' accounts. Typically, 20% of the stolen assets go to the Drainer developers, while 80% go to the scammers using the service.
The scam group that purchases this malware service primarily implements fraud by creating phishing websites that impersonate well-known Crypto Assets projects. They exploit highly convincing Twitter accounts to post a large number of fake airdrop claim links in the comments section of official Twitter posts, luring users into phishing websites. Once users let their guard down, they may suffer financial losses.
social media account hijacking
In addition to selling malware, social engineering attacks are also one of the common tactics used by Drainers. Hackers steal Discord and Twitter accounts of high-profile individuals or projects to post false information containing phishing links to steal user assets. They often trick Discord administrators into opening malicious verification bots or adding bookmarks with malicious code to steal permissions.
After successfully gaining access, hackers will also take a series of measures to prolong the duration of the attack, such as deleting other administrators, setting malicious accounts as administrators, and making the main account violate regulations. Hackers use stolen social media accounts to send phishing links, tricking users into opening malicious websites and signing malicious signatures, thereby implementing asset theft.
Ransomware Services
A certain Russian ransomware service organization provides services such as domain, malware development, and maintenance, retaining 20% of the ransom from victims infected by its code; users of the ransomware service are responsible for finding ransom targets and receive 80% of the ransom amount ultimately paid to the organization.
According to the U.S. Department of Justice, the gang has attacked thousands of victims worldwide since it first appeared in September 2019, extorting over $120 million in ransom. The U.S. recently charged a Russian man as the leader of the ransomware group and froze more than 200 cryptocurrency accounts believed to be linked to the gang's activities, while imposing sanctions on the organization.
The Huge Dangers of Drainers
For example, in a case of a victim related to Drainer recorded by a certain data platform, the victim authorized a phishing website and had Crypto Assets worth $287,000 stolen. This phishing website was launched on social media during the early days of a public chain, luring users to claim airdrops. The domain name of the phishing website differed from the official website of a well-known project by only one letter, making it very easy to confuse.
According to the stolen transaction hash provided by the victim, it can be found that the initiator of the stolen transaction is Drainer. After the theft, 36,200 pieces of a certain coin entered Drainer's fund collection address, while 144,900 pieces entered the hacker's address, completing the profit distribution of 80/20. According to data platforms, the fund collection address involved in this case has had a flow of as high as 8,143.44 ETH and 910,000 USDT from March 2023 to the present.
Statistics show that in 2023, Drainer has stolen nearly $295 million in assets from 324,000 victims. Most Drainers only started to become active last year, but they have already caused significant economic losses. Only a few well-known Drainers have stolen hundreds of millions, highlighting their severe harm and wide-ranging impact.
Conclusion
With the announcement of retirement by a well-known Drainer team, a new Drainer team immediately announced that they would take over. Whenever one Drainer exits, a new Drainer takes their place, leading to a cycle of phishing activities that alternately rise and fall, creating a vicious circle.
In the face of rampant criminal gangs, building a secure encryption environment requires joint efforts from multiple parties. As users, it is crucial to remain vigilant and enhance awareness of prevention. At the same time, relevant platforms and institutions should also strengthen security measures to jointly combat such illegal activities, creating a safer and healthier environment for the Crypto Assets ecosystem.