- Topic1/3
19k Popularity
38k Popularity
22k Popularity
6k Popularity
174k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is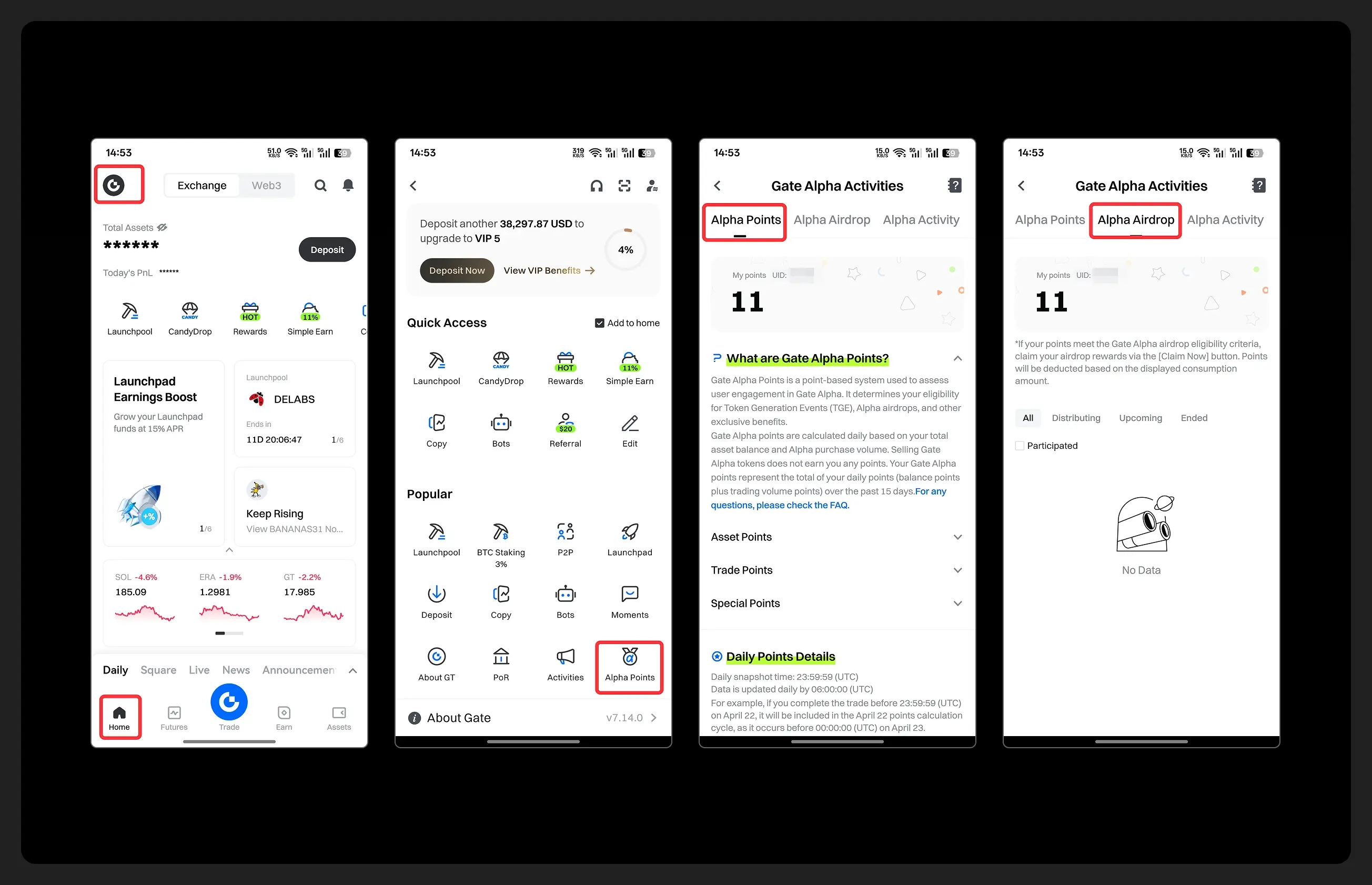
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Move language reference security module discovered a new integer overflow vulnerability
A new integer overflow vulnerability has been discovered in the Move language reference security module.
Recently, during an in-depth study of the Move language, a new integer overflow vulnerability was discovered. This vulnerability exists within the reference safety verification module, and its triggering process is quite interesting. This article will provide an in-depth analysis of this vulnerability, as well as introduce relevant background knowledge of the Move language.
The Move language will validate the code units before executing the bytecode, and the entire validation process is divided into 4 steps. The vulnerability discovered this time occurs in the reference_safety step.
The reference safety verification module is mainly responsible for checking whether there are dangling references, whether mutable reference access is safe, and whether global storage reference access is safe, etc. The verification process starts from the analyze_function function, verifying each basic block.
In the Move language, a basic block refers to a sequence of code that has no branching instructions other than the entry and exit. The system determines the basic blocks by traversing the bytecode and looking for all branching instructions and loop instruction sequences.
The Move language supports two types of references: immutable reference (&) and mutable reference (&mut). The reference safety module scans the bytecode instructions of each basic block in the function to determine whether all reference operations are legal. The verification process uses the AbstractState structure, which contains two components: borrow graph and locals, to ensure the safety of references within the function.
During the verification process, the system will execute the basic block code to generate the post state, and then merge the pre state and post state to update the block state. If the state changes and a loop exists, the basic block will be executed repeatedly until the post state equals the pre state or an error occurs.
The vulnerability occurs in the join_ function. When the combined length of the parameters and local variables exceeds 256, using the u8 type to iterate locals can lead to integer overflow. Although the Move language has a process to verify the number of locals, it only checks the number of local variables and does not include the length of the parameters.
This integer overflow may lead to a denial of service attack. An attacker can construct a loop code block that exploits the overflow to change the block's state. When the execute_block function is executed again, if the index that the instruction needs to access does not exist in the new AbstractState locals map, it will cause the system to crash.
To demonstrate this vulnerability, we can construct a basic block that contains unconditional branch instructions. By setting appropriate parameters and the number of local variables, we can overflow the locals map length to 8. On the second execution, attempting to access a non-existent offset will cause a panic.
This vulnerability reminds us that even well-designed languages can have security risks. For the Move language, it is recommended to add more check code at runtime to prevent unexpected situations. Currently, security checks in Move mainly occur during the verification phase, but once the verification is bypassed, it could lead to more serious issues.
As pioneers in the security research of the Move language, we will continue to explore relevant security issues in depth and contribute to the healthy development of the Move ecosystem.